Table of contents
- How does a block get added in a blockchain?
- What is MEV?
- 1.Based on transactions
- 2. Time Bandit Attacks :
- 3. Just in time(JIT) liquidity :
- 4. MEV in NFTs:
- 5. Long Tail MEV:
- MEV in Ethereum vs New blockchains
- MEV in POS
- IS MEV Good or Bad?
- MEV in Rollups
- Why is it hard to reduce negative externalities of MEV?
- Current MEV Mitigation Landscape
- Cross Domain MEV
- Future of MEV
Why are you paying an invisible tax every time you send a transaction on a blockchain? What could be the reason behind your profitable transaction getting reverted? What other incentives does a miner have apart from block rewards?
These are some really important questions that can be answered after understanding Miner Extractable Value or MEV.
This article explains MEV and it’s importance in Web3’s evolution. It touches upon the following
MEV definition and entities involved
Super cool strategies for extracting MEV through real life examples
Good and Bad MEV
MEV in POS Blockchains (Eth 2.0)
MEV in Rollups
Why is it hard to solve?
Current MEV Mitigation Landscape
Cross Domain MEV
Future of MEV
How does a block get added in a blockchain?
Before we dive deeper into what MEV is, let’s first quickly go through how a transaction get’s added to a proof of work blockchain like Ethereum.
User sends a transaction which is propagated to every node on the underlying peer to peer(p2p) network.
The transaction then shows up in Ethereum client public mempools. A mempool or txpool can be thought of as a waiting room where transactions wait to be added to a future block.
Miner selects transactions based on incentives(gas fee/transaction fee) and adds it to his block.
The block is added to the Ethereum chain if proof of work is won by the miner

What is MEV?
MEV or miner extractable value or maximum extractable value is a measure of the maximum profit a miner (or validator) can make because of certain unique powers they have while producing a new block. These powers are the ability to arbitrarily include, censor or re-order transactions in a block they are producing. As a result, a miner can replace the arbitrage opportunity a user has identified by their own wallet address and can censor his transaction keeping the entire profits to themselves. Another popular version of extracting MEV is facilitated by bots who participate in something known as a priority gas auction (PGA). As miners are incentivised to order transactions based on gas fees, bots take advantage of this to exploit and frontrun these transactions by placing a slightly higher gas fee than the user and thereby getting their transaction executed before the user’s. I like the term maximum extractable value as it is a bit more intuitive because of non-miners being able to extract it as well. This term was first coined by Phil Daian in the paper- Flash boys 2.0 where frontrunning, consensus instability and game theoretic strategies deployed by bots in PGA are discussed in detail.
Total MEV present today can’t be measured, however, transactions happening through Flashbots give us the lower bound of MEV.
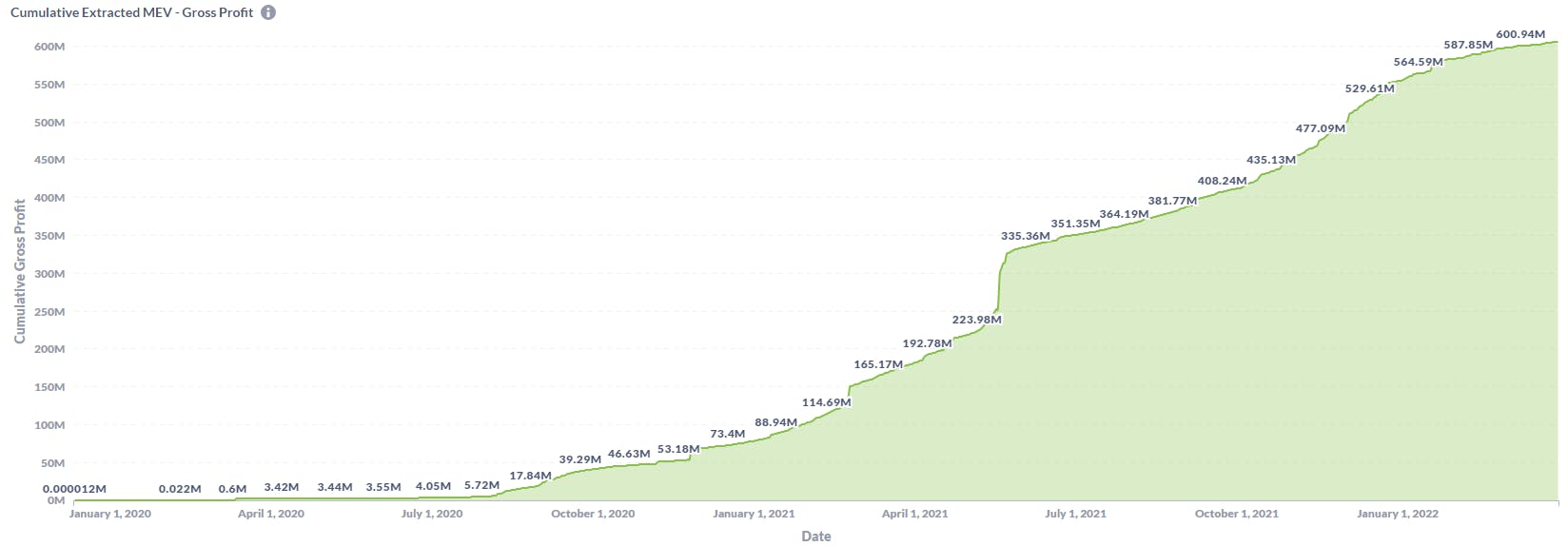 (source)
(source)
The Flashbots explore dashboard measures the lower bound of total MEV activity happening. The distribution of MEV extraction by bots or searchers and by miners is skewed with the majority being extracted by bots. Gradually this will shift towards miners especially when Ethereum transitions into a Proof of State blockchain where validator incentives will be heavily incentivised by participation in MEV(discussed later).
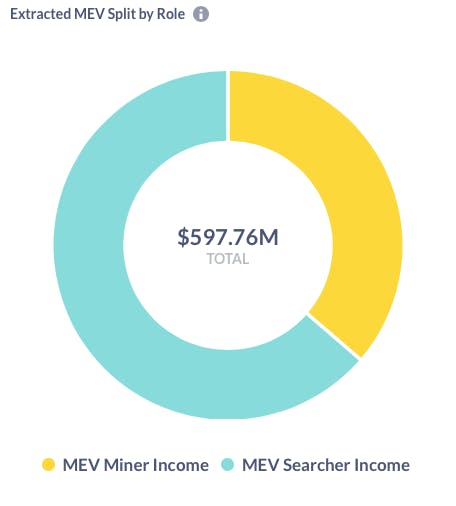
Let’s try to classify different MEV strategies and understand them through some examples :
1.Based on transactions
1.1 Relative ordering of transactions :
In these types of MEV strategies, MEV is extracted by placing a new transaction relative to a particular transaction in a block. The transaction could be placed just before(frontrunning), or after(backrunning), or both(sandwich attack) in order to extract MEV.
1.1.1 Frontrunning :
It is the process in which a bot or a miner identifies a transaction that represents a profitable opportunity like an arbitrage and mimics that transaction with a higher gas fee in order to get their transaction included first. Using the example provided in the article MEV and Me, let’s suppose there is an arbitrage opportunity of $10,000 on Uniswap caused by a price slippage following a large trade. A user has identified this and has sent a transaction to capture this arbitrage opportunity
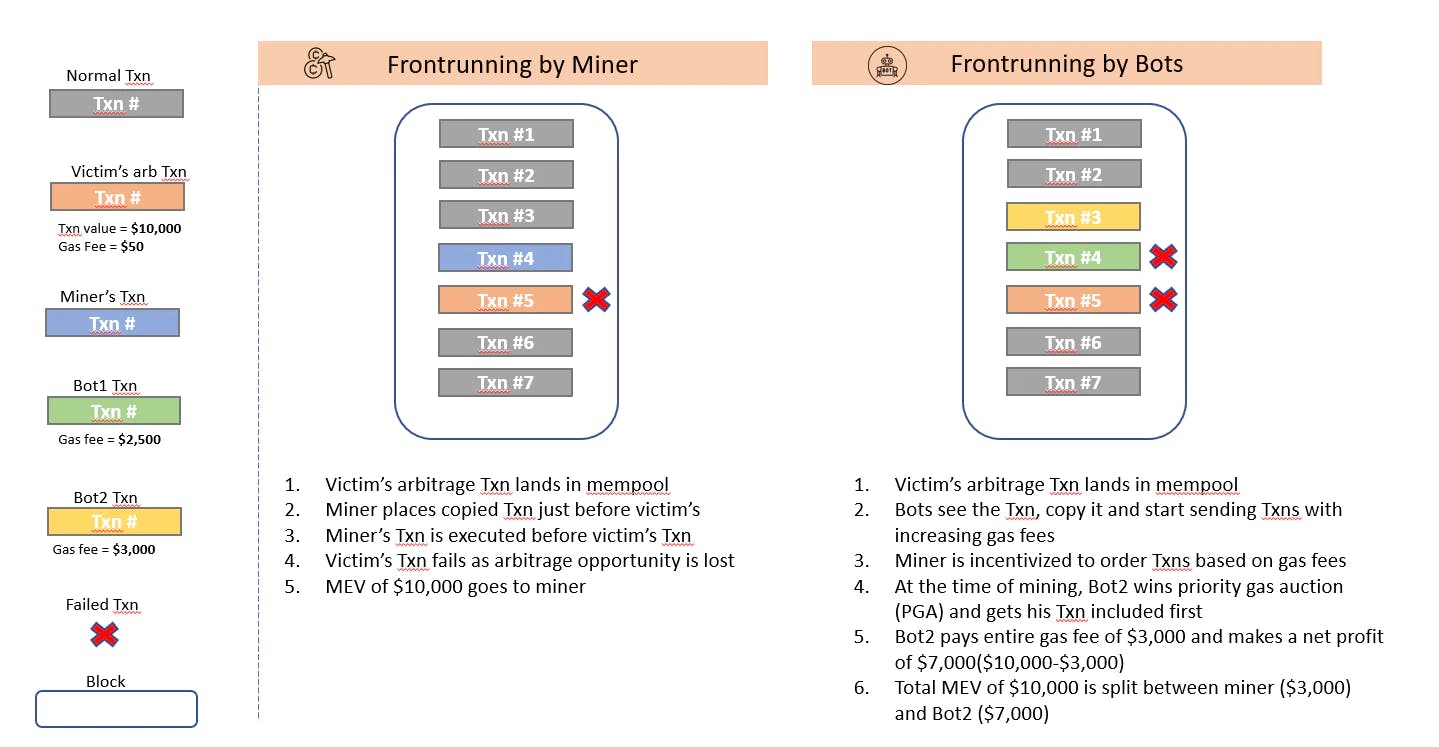
a) Upon seeing this transaction in the mempool, a miner can copy the relevant fields of this transaction (like data fields, the transaction being sent to Uniswap etc) and include his copied transaction before the original one to guarantee that his transaction gets executed first. The miner also has control over inclusion of transactions in the block he is adding. He can choose to censor the original transaction by not including it in the block. By only keeping his copied transaction in the block, he can keep the entire profit of $10,000 to himself. The total profit of $10,000 is the MEV which in this case will go to the miner. It is worth noting that the arbitrage opportunity in most cases would be lost after miner’s transaction gets executed and the victim’s transaction would fail
b) If the miner does not copy the transaction himself, Bots will copy the transaction and place a higher gas fee. Miner gets the gas fee for every transaction and is therefore incentivised to order transactions based on gas fees. This means that among identical transactions, the one with a higher gas fee would be placed first.
Let’s say Bot1 and Bot2 have identified this profitable transaction and are both trying to get their transaction in front. This will give rise to an auction where each of the bot will repeatedly submit transactions with increasing bids (gas fee) for transaction priority. This is known as a Priority Gas Auction(PGA). The different PGA strategies deployed by bots is explained in great detail in Flash boys 2.0 but for this example, let’s say Bot1 and Bot2 engage in a counter-bidding strategy. This means that they will observe each other’s bets and react to it by placing a higher bid.
Bot1 bids $1000
Bot2 bids $1500
Bot1 bids $2500
Bot2 bids $3000
By the time this block is mined, Bot2 would be the winner of the auction and will have front run both the user and Bot1. Bot1 will pay gas for the attempted execution(a far smaller sum than Bot2). The total MEV here is again $10,000 out of which, Bot2 gets $7,000 and $3,000 goes to the miner
1.1.2 Backrunning:
In this strategy, MEV is extracted by placing a new transaction right after a particular transaction. What kind of transactions are these and why would someone want to place a transaction right after it? Let’s take an example. Consider a liquidity pool of ETH/COMP tokens on a decentralized exchange like Uniswap. If Alice buys COMP tokens by selling ETH, the price of COMP tokens on Uniswap will increase and the price of ETH will decrease because of the supply and demand dynamics(price calculated by constant product AMM). This is an arbitrage opportunity where one can buy ETH at a lower price on Uniswap and sell it on other DEX’s for a profit. In order to do so, bots or miners would want to place their transaction right after Alice’s transaction.
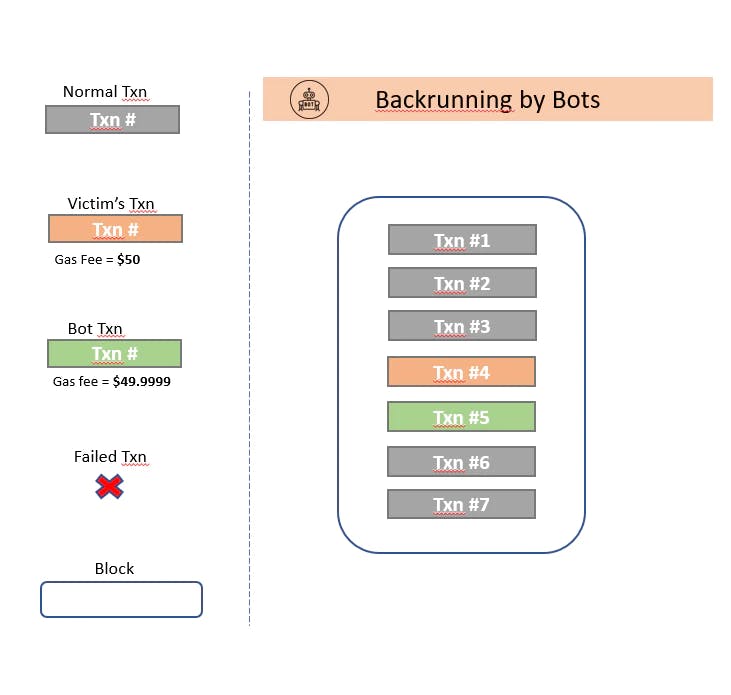
How do they do it? After Alice’s transaction has been identified, a bot will send multiple transactions of buying ETH with a gas fee same or slightly lower than that of Alice’s. As miners order transactions based on gas fees, the more transactions you send, the more chances you have of ending close to Alice’s transaction. It is also referred to as sniping a transaction within a block. This however, creates a lot of network congestion. This Dune Analytics dashboard shows that around $316 million has been used in backrunning gas consumption.
This strategy has been used to make profits after an Initial DEX offering(IDO) of multiple projects. Let’s look at a real case example.
A defi protocol named bZx announced that they would launch their BZRX tokens on Uniswap on 13/07/2020. A trader was able to buy 40% of the BZRX tokens in supply. This caused an increase in it’s price and attracted other people to buy even more, pushing the price even higher. The trader then started selling the newly minted tokens to make a huge profit. The profit margin depended on how early he was able to buy the new BZRX tokens.
He created a smart contract and added 650 ETH to it. He then created 732 addresses with balances enough to cover the gas fees of invoking the smart contract.
Following the IDO launch, he sent transactions from each of the 732 addresses with the same gas fees as that of the IDO launch transaction (60 gwei). All transactions that were placed before the IDO launch were rejected because invoking the smart contract to buy BZRX token before it’s launch would be invalid. He was able to get a transaction placed right after the transaction of IDO launch. All other transactions failed because this successful transaction invoked the smart contract and bought BZRX tokens worth 650ETH using up all of the smart contract’s balance.
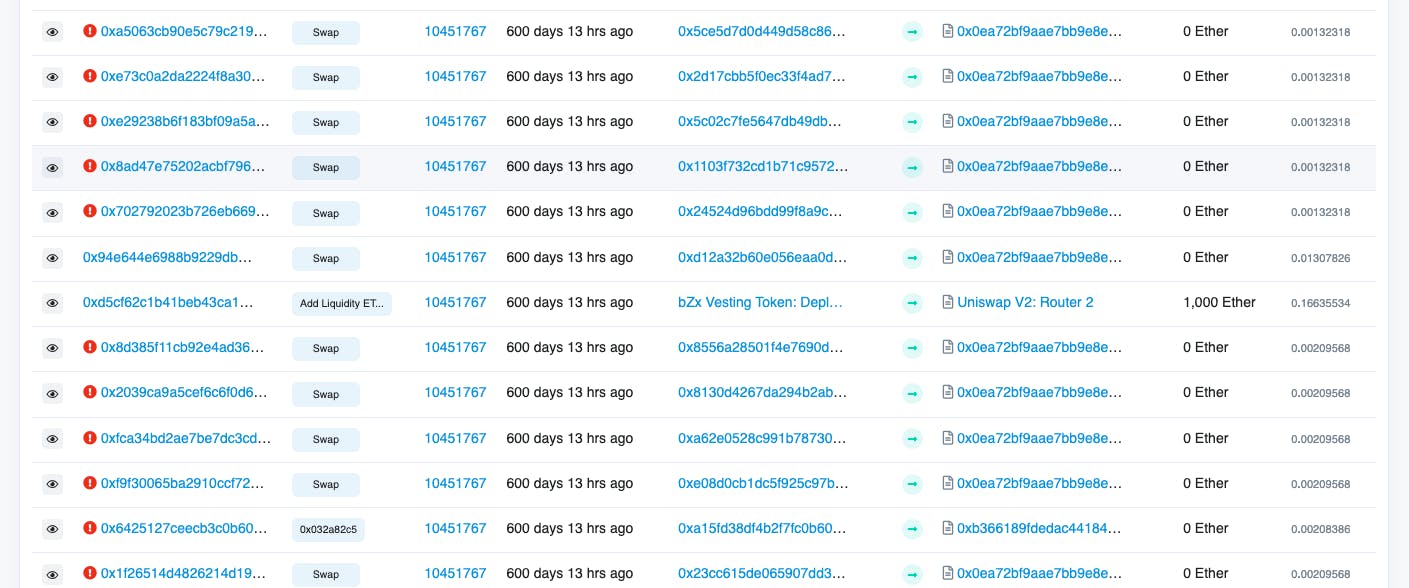
In the image above(source), we can see all transactions being sent to the same address(smart contract). He was able to backrun the IDO transaction and purchase ~2M BZRX tokens.
After waiting for the prices to rise, he began selling the BZRX token for a huge profit.
The entire strategy deployed by the trader can easily be deployed by a miner as he can place a BZRX buy transaction right after the IDO launch.
1.1.3 Sandwich attack :
In this strategy, MEV is extracted by placing a transaction just before and just after a particular transaction. The transaction is sandwiched by 2 transactions placed before and after it.
Let’s take an example. Suppose a user sends a transaction to buy 10 Eth from Uniswap at a price of $2500. Because of the volatility in price of Ethereum, he would set a ‘slippage tolerance’ which is a limit of the maximum price fluctuation he can live with(if slippage tolerance is 1%, he is willing to buy 10Eth at a price of $2525) . Now bots or miners can sandwich the transaction and make a profit in these steps :
- Bot or miner would buy Eth just before the user and will increase the price of Eth. Using the pricing formulas used in Uniswap, they can calculate the exact amount of Ethereum to buy such that the price does not exceed the slippage tolerance( $2525) of the user. If the price exceeds tolerance, the user’s transaction will get reverted.
- User’s transaction will land on chain and he would get 10 Eth but at an inflated price. His transaction will further increase the price of Eth.
- Bot or miner can now sell their Eth at a higher price and make a profit
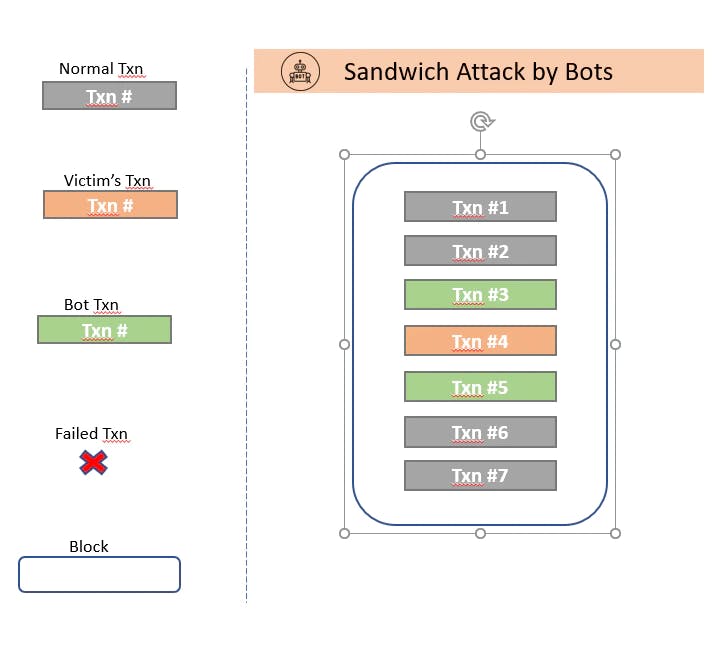
Let’s look at a real example:
- Sandwich bot gets in front of the user’s transaction and buys STXY tokens for $108 worth of WETH. This increases the price of STXY tokens
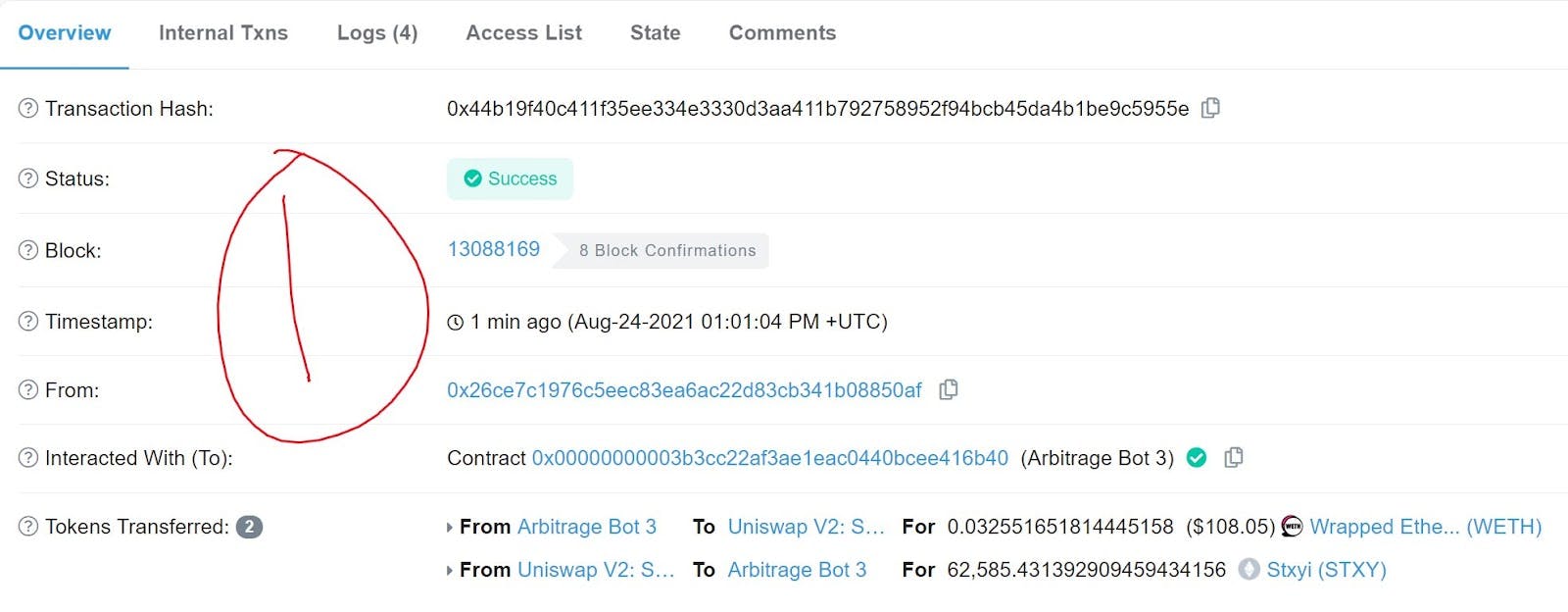 (source)
(source)
- User’s transaction lands on chain and further raises the price of STXY tokens
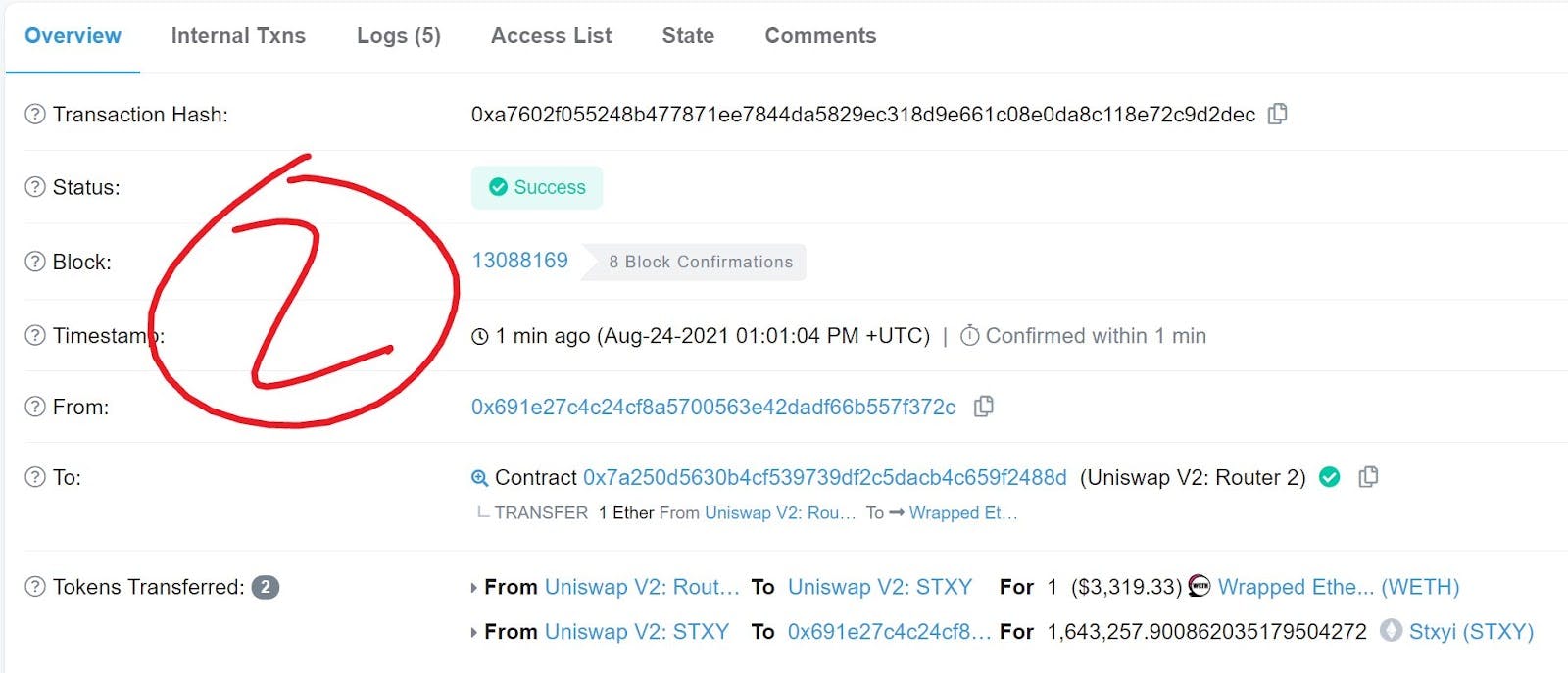 (source)
(source)
- Bot immediately sells STXY at this higher price (total $145) and makes a profit.
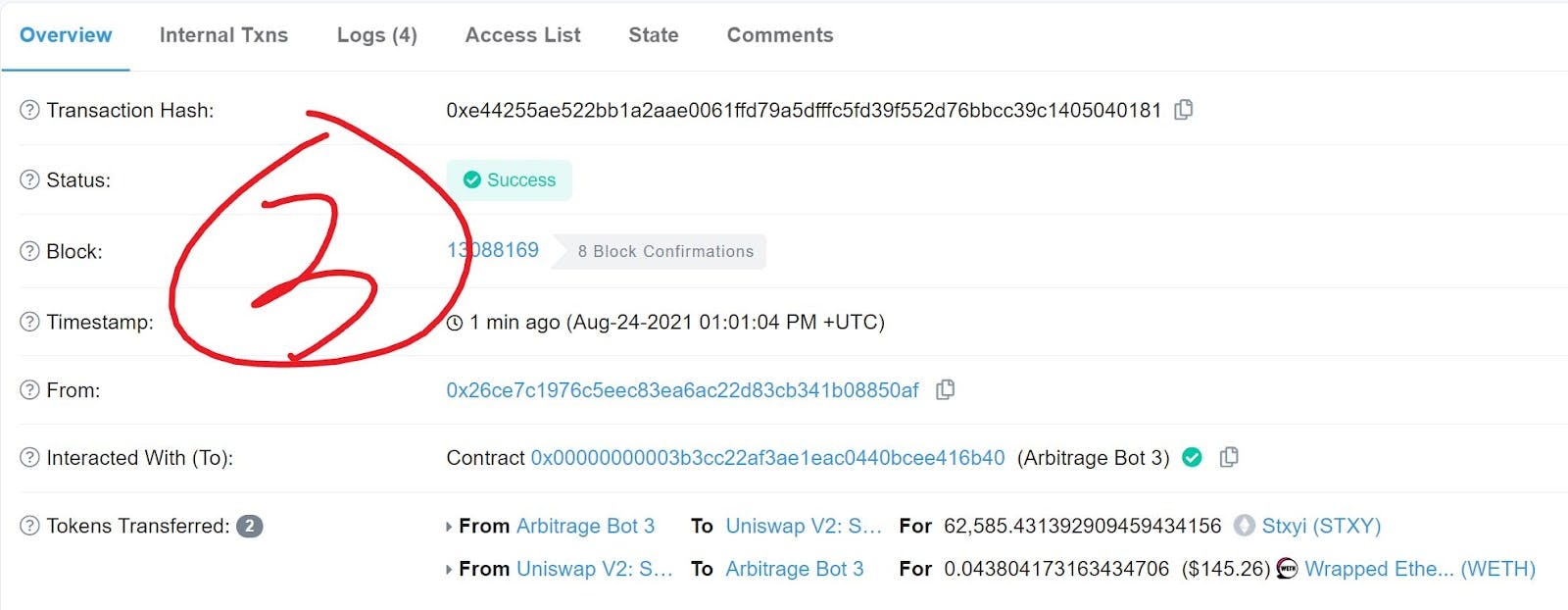 (source)
(source)
These attacks are also carried out with the help of flashloans so that the process is not very capital intensive and the sandwich bot or miner can execute this strategy with a leveraged position.
1.2 Absolute Ordering of Transactions:
In these types of MEV strategies, a bot or miner is not concerned about placing a transaction relative to a given transaction(right after or before). Only the absolute position inside of the block is of relevance. A miner can therefore choose to not include a given transaction in the block and still extract MEV
1.2.1 Based on other transactions data :
A miner or a bot can identify a profitable transaction, copy it and make sure that it gets included before (not immediately before) the profitable transaction. An example of this is given in the famous article called ‘Ethereum is a Dark Forest’. A user accidentally sent Uniswap liquidity tokens to the pair contract. A transaction was sent to recover these tokens but a bot identified this, copied the data and placed its own transaction with a higher gas taking away all the funds. Please read the legendary article for an in-depth understanding.
One thing to note here is that the bot did not have to place his order right before the given transaction. A miner could have achieved the same if he would have identified this opportunity.
1.2.2 Not based on other transactions data :
In some cases bots or miners would not need to look at the transaction of others to identify a profitable MEV opportunity. The opportunity is known to all and only needs to get executed first in order to reap profits.
A Defi lending protocol allows a user to borrow assets by depositing collateral. This type of lending is always over collateralized meaning that the value of deposited collateral is higher than what is being lent. When the value of this collateral drops below a certain threshold(which is set by the protocol), it gets liquidated. The protocol allows anyone to liquidate these positions and incentivizes this by paying a flat fee to the liquidator or letting him keep a portion of the collateral. The liquidator repays the loaned amount and gets to keep the borrower’s collateral and this is usually facilitated by flash loans so that it is not capital intensive. The value of the collateral being higher than the loaned amount acts as an incentive for liquidators.
Once someone identifies such a liquidation, it is just a game of how competitive his gas fee is in order to win a prioritized transaction ordering. A miner, like in cases mentioned previously, has the edge of including his liquidation transaction first.
This extraction is not dependent on placing transactions relative to other transactions. Liquidation opportunities can be identified before they happen and hence could be executed without copying other transaction’s data. Normal frontrunning bots would still operate here by copying these transactions but that is not the only way to extract MEV in this scenario.
Robert Miller of Flashbots has written a detailed process of how he built liquidation smart contracts when he found out that a couple of Synthetix smart contracts were going to be deprecated and the loaned amounts in those smart contracts would need to be liquidated.
2. Time Bandit Attacks :
The amount of MEV being extracted is growing every day. There have been multiple instances of a single block having millions of dollars worth of MEV. In such a scenario, extracting MEVs is much more lucrative than the block rewards you get in mining a block. A time bandit attack is when a miner attempts to rewind the history of blocks in order to extract the value contained in previously mined blocks. For example, if a miner sees that in the 3rd latest block, there is an MEV opportunity worth $1mil, he can attempt to mine that block himself and get the associated MEVs. He would then have to mine the consecutive blocks and win proof of work very quickly so that he has the longest chain and the blockchain’s new state that he has created becomes the valid one. In POW blockchains, this means that he would need at least 51%(this is why it is also known as 51% or majority attack) of the total computational power(hash rate) existing across all mining nodes. This obviously gets more and more difficult as network participants grow and the computational power gets decentralized. It is therefore easier to perform such an attack in blockchains with lower hash rate securing it. Monacoin and Zencash have been victims of such an attack.
Such attacks are serious threats to blockchains as they cause consensus instability.
3. Just in time(JIT) liquidity :
This is a relatively new form of MEV being extracted by utilizing the design of UniswapV3. UniswapV3 has introduced new changes like having different AMM curves for different price ranges of assets. A full understanding of the implication of these changes for different actors should be gained through their whitepaper or blog. I will explain parts of it necessary for understanding this MEV strategy.
In UniswapV2, liquidity providers(LP) provided liquidity for assets in the entire price range of 0 to infinity. As rewards for providing liquidity, they would get a percentage of all transactions as transaction fees.
In UniswapV3, LPs can provide liquidity in a fixed price range of 0 to k.
When the price of the asset moves outside the provided range (0 to k), they generate no transaction fees.
A tighter range would mean that the probability of the asset price moving outside of that range is higher making it more risky
A tighter range will also mean that LPs would get rewarded with a much higher transaction fee.
Now, suppose a user sends a transaction of buying ETH for $1mil USDT on UniswapV3. A bot or a miner can frontrun this transaction by providing liquidity worth $1mil in the tightest possible range earning an enormous transaction fee and removing their liquidity immediately after the buy transaction.
4. MEV in NFTs:
Not many MEVs have been extracted in NFTs and they remain a part of ‘Long Tail MEV’ discussed later. Strategies discussed above could be applied here as well. Similar to liquidity sniping at the time of IDO launch of a new coin, bots can also purchase enough NFTs of a collection at the launch price and sell it later when the price increases. People have been exploited because of accidentally setting a lower minimum auction price. Here is a thread describing a sandwich attack on a cryptopunk. The owner of that cryptopunk had set his minimum price to 0, which the bot then exploited by purchasing it at only 1 wei and selling it to a bidder who had bid 26Eth for it.
5. Long Tail MEV:
Most of the strategies discussed above have been around for a while now. People have been innovating on them in fascinating ways and exploiting unexplored territories of MEV. Let’s look at some examples:
a) Convex Finance boosts Curve Finance (CRV) rewards by reinvesting CRV back into your position so that your rewards compound over time. Convex Finance does it in a decentralized way by offering 1% of the reinvested CRV to anyone who attempts to do so. Anyone doing so, would spend gas for sending this transaction but would get 1% of CRV reinvested. A bot was frontrunning every such transaction by increasing the gas price by 0.001. This was incentivised only when CRV rewards are greater than Eth gas fees. If another bot starts a PGA, then the profits to bots will decrease. This is when 2 players colluded off chain and reached an agreement to split MEVs and not start a bidding war by paying for transaction fee.
b) A couple of weeks back, an owner of etherRock #44 (an NFT project) accidentally set the price of his NFT at 444 wei instead of 444 Eth. A bot was able to backrun this in the same block and is now trying to sell it at 234Eth.
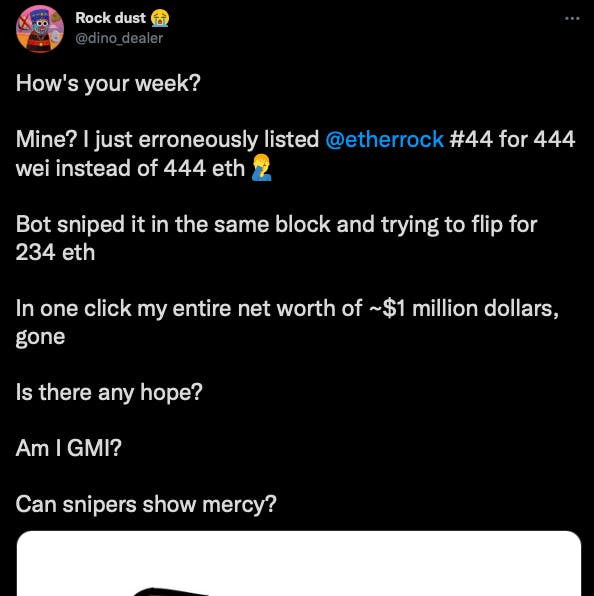 (source)
(source)
MEV in Ethereum vs New blockchains
Ethereum has a very diverse and evolved application layer meaning that it has a lot of different dapps built on top of it. This means that the amount of value as well as the volume of transactions are extremely high. As this ecosystem is gaining more depth with growing user adoption and Total value locked, MEV opportunities are rising exponentially. The diverse nature of this ecosystem also fuels new and dapp specific vectors of attack.
Relatively newer blockchains with less evolved application layer would have lower opportunities for MEV extraction. As more dapps are built on them, MEV opportunities will also increase because of increased value flux through these dapps. Newer blockchains also face the threat of consensus instability incentivized by MEV
MEV in POS
Unlike POW, blockchains having a proof of stake (POS) consensus mechanism do not need to solve cryptographic hash functions. In POS, validators vote to reach consensus and are responsible for securing the network. Each validator would stake some amount of coins which acts as a security deposit that can be slashed for malicious behaviour or downtime. They get rewarded with block rewards for good behaviour.
For each block, one validator is pseudo-randomly chosen to ‘propose’ a block and all other validators ‘attest’ or vote on the proposed block being valid. Block ‘proposers’ and block ‘attesters’ get rewarded for accurately performing their duty and get penalized for failing to do so.
Like POW miners, POS block proposers possess the same powers of arbitrarily including, censoring or reordering transactions in the block they are proposing. Hence MEV is still present in POS systems but with different dynamics. The pseudo random allocation of block proposers means that MEV opportunities would not be present to every validator in every block being produced and will depend on how lucky they are in being selected to propose a block. Their MEV profits would also depend on the MEV opportunities present in the transactions available to them while producing a block.
How will MEV affect validator incentives? Flashbots have released an article explaining this for Ethereum when it transitions from POW to POS(Eth2). They have used an analysis on block rewards in Eth2 by pintail in this article. A thorough reading of both is recommended to understand the effects of MEV in Eth2. I will just use their conclusion to emphasize how big of a role MEV will play in Eth2 and similar POS blockchains.
Eth2 reaches consensus after each epoch. Each epoch contains 32 slots, which are 12sec long. A maximum of one block can be produced in a slot(it may be 0 if the proposer is offline).An epoch would thus end after (32*12/60) = 6.4 minutes.
Since a slot is 12 seconds long, in a single year, the no.of slots = total seconds in a year / 12
= 31556952/12 = 2629746
Each validator would have an equal chance of being selected as a proposer. If we consider 100,000 validators, the probability of being selected as the proposer of a slot is 1/100,000
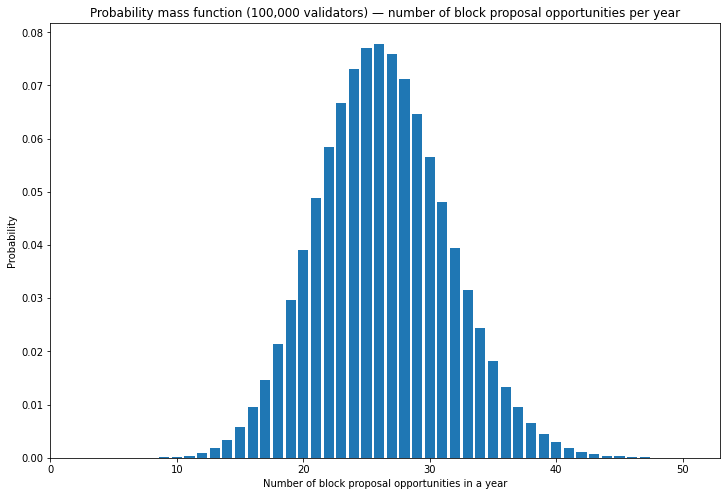
No. of block proposer opportunities is given by a binomial distribution. The probability mass function would be :
 (source)
(source)
With 100,000 validators
Unluckiest 1% validators will have the opportunity to produce at most 15 blocks in a year
The median validator will have the opportunity to produce 26 blocks in a year
Luckiest 1% validator will have the opportunity to produce at least 39 blocks in a year
1. When average realized MEV ( lower bound of MEV seen in Flashbots run clients ) is added to each block
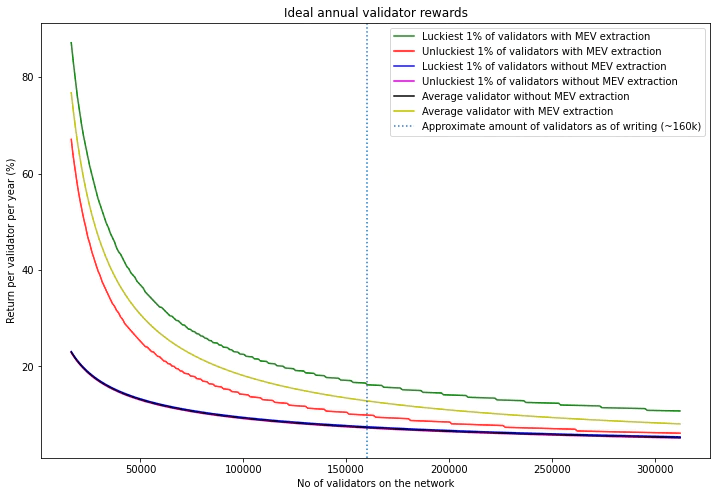
MEV amplifies inequality created from block proposer luck
Validators with MEV have higher returns than validators without MEV
Unluckiest 1% validators extracting MEV have higher returns than the luckiest 1% validators not extracting MEV
2. When MEV opportunities present in blocks is modelled to be non-uniform and added to validator rewards
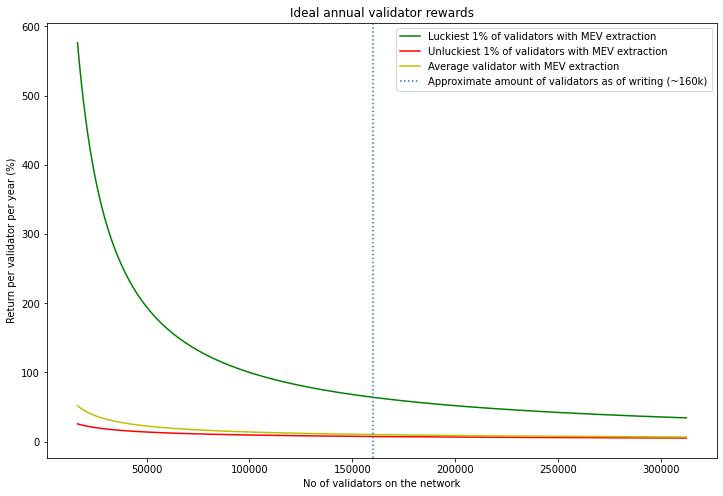
The gap between luckiest 1% and unluckiest 1% validators are even more amplified when we account for a non-uniform distribution of MEV across different blocks
The disproportionate increase in returns incentivises validators to participate in extracting MEV.
IS MEV Good or Bad?
In many cases, MEV driven incentives are actually beneficial for the functioning of blockchain and applications built on top of it. For example, arbitrage bots help in making the price of a coin, the same across the market. Similarly, Liquidation bots enable a lending protocol to maintain system solvency. In the example discussed earlier about Convex Finance, the reinvestment of CRV rewards in a decentralized way was achieved by bots facilitating those transactions. These are examples where MEV extraction incentives add value to the blockchain. MEV revenues also incentivise people to stake in their coins. This could allow to reduce inflation rate to achieve the same level of network security. However, as seen from many examples above, there are a lot of negative externalities arising out of MEV.
This ruthless game of building innovative strategies to extract MEV is being played at the expense of a normal user. A normal user unaware of such negative externalities, is buying at an inflated price imposed as a result of these strategies. He is unaware of the forces at play when his transaction remains pending for a long time only to get cancelled at the end. PGA, frontrunning and backrunning cause a lot of network congestion. During times of volatility, MEV opportunities rise up (more volatility → more opportunities like arbitrage) and as everyone starts bidding with priority gas fees to obtain transaction priority, less gas is available for non-priority gas fee transactions. Because of this, gas prices of non-priority transactions also increase. Time-bandit attacks driven by MEV incentives cause consensus instability and threaten the security of a blockchain.
MEV in Rollups
Generally, Rollups allow transactions to be executed off-chain, publishing on chain, only the bare minimum information required to show validity of transactions. Rollups as a scaling solution separates transaction ordering from execution.
In order to assess MEV in different rollup mechanisms, it is important to understand the distribution and barriers of powers governing MEV i.e ability to see content of transactions, order them, include your own transaction or censor someone else’s transaction. This would determine the dynamics of MEV in rollups.
Who is the Sequencer?
If the sequencer is a single entity such as in optimistic and zk rollups, he would have the ability to order, censor and include transactions. In such a scenario, MEV opportunities shift from layer1 miners/validators to the layer2 sequencer. Optimism is planning to implement an MEV auction where the transaction ordering rights of a rollup batch would be auctioned. There are concerns that this would lead to off-chain collusion between sequencers. You can find more on this here. Arbitrum does its transaction ordering through ‘Fair Sequencing’. It decides transaction ordering by adding a BFT layer on top of layer1 consensus. Transaction ordering is agreed upon by participants instead of a single entity deciding them. In this case, MEV opportunities simply move to a pre-consensus layer
Are transactions encrypted?
Different types of encryption would impact the dynamics of MEV in different ways. Threshold encryption (like fair sequencing) would add a BFT layer on top of layer1 and the MEV would shift to this layer instead. In Time Lock encryption(like verifiable delay function (VDF)), the data remains encrypted for some time and hence obstructs transaction ordering. It however delays execution and may deter even good MEV transactions.
How is ordering done?
As seen above, if the ordering is done by fair sequencing as compared to a single sequencer doing it, MEV shifts to participants of the BFT layer on top of layer1 consensus. Some methods may randomize transactions in a batch but it would still be prone to transaction censoring ( sequencer can only include his transactions in a batch and censor every other transaction).
Why is it hard to reduce negative externalities of MEV?
As seen earlier, currently, the proportion of MEV extracted by bots is much higher than what is being extracted by miners. MEV strategies that are specific to miners would be exploited more as miners start participating more actively. It is very hard to design a balanced incentive mechanism for miners, traders and users (reduce negative externalities). MEV mitigation usually comes at the cost of decentralization and/or efficiency. Reducing miner incentives would lead to them colluding off chain. Encryption of transactions introduces overhead and time delays whereas application level mitigation usually leads to some form of centralization.
MEV can’t be completely eliminated(there is no free lunch) but it can be reduced to a level which is inherent and not harmful to the users/security/efficiency of blockchains. This could be done by better design of encryption and rollups that help mitigate MEV without compromising decentralization and efficiency. Dapp builders should address this issue along with other audits and stress test the possible vectors of attack possible in the product they are offering. They should involve the community to address these issues. They should also inform their users and bring more transparency around negative externalities of MEV. Flashbots research as well as other services helps bring more transparency to these predatory MEV behaviour.
Current MEV Mitigation Landscape
MEV mitigation landscape can be broadly divided into encryption based, network based and application based. Application based solutions primarily focus on Dex based MEV opportunities as they constitute the majority for MEV based activity. Network level mitigation consists of mempool privatization and segregation. I have also included some rollup solutions in encryption based solutions among others that redefine the manner of transaction ordering.
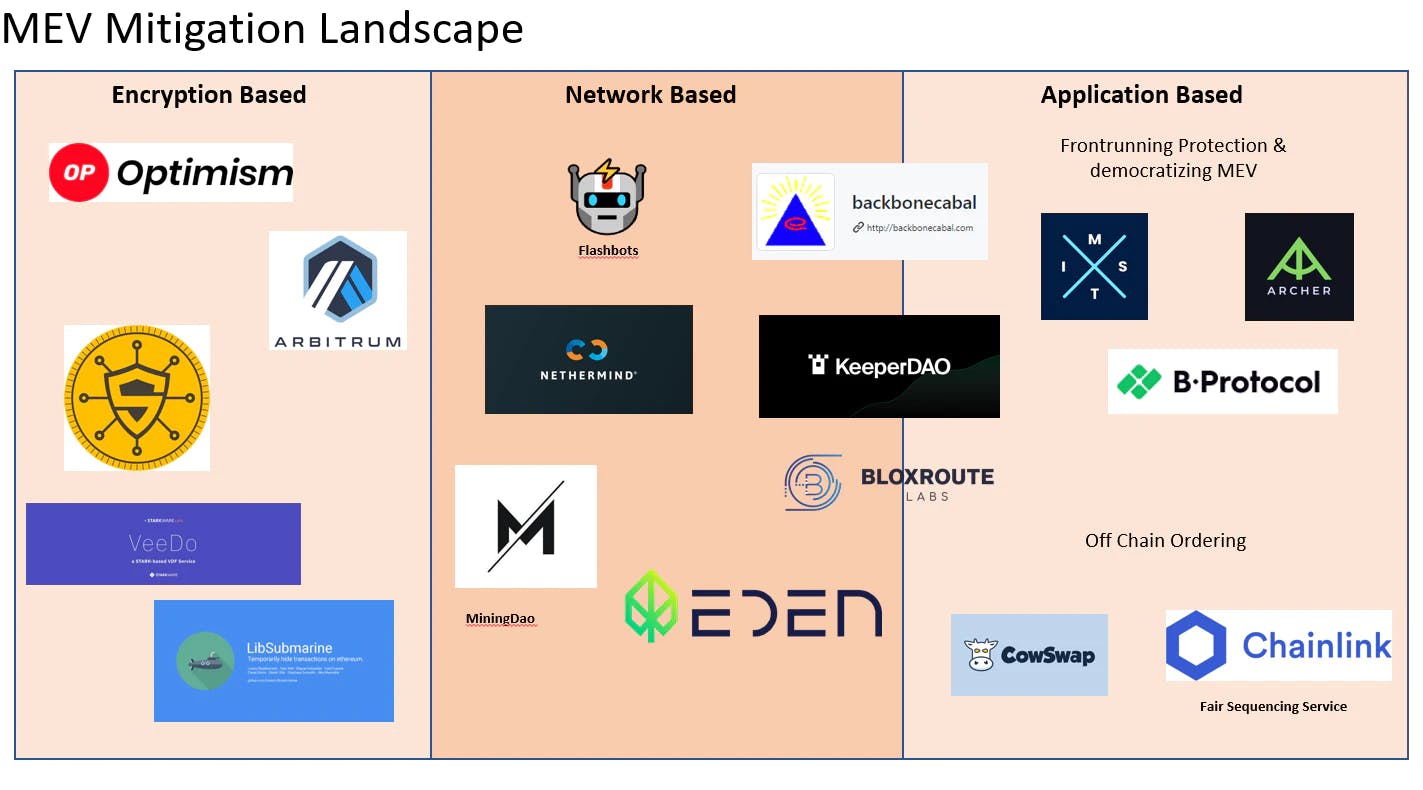
Application Based:
mistX: mistX is a DEX that allows frontrunning protection to users. They are natively integrated with Flashbots and send transactions through Flashbots bundles. The user does not have to pay gas fees on failed transactions. If your trade gives rise to an arbitrage opportunity, it is executed by third party services and a portion of it is returned back to the user as instant Eth cashback rewards. It also provides an easy to integrate API for dapp builders to include frontrunning protection for their users
Archerswap: It is a DEX extension that provides frontrunning resistance, zero slippage swaps, zero cost order cancellations and zero cost transaction failure. Using Archer relayer, users bypass the public mempool and negotiate for blockspace directly from miners by paying them a tip instead of gas fees. Tip is paid to the miner only if the transaction is successful.
Cowswap: Cow Swap is built on top of gnosis protocol. It is a DEX aggregator that operates on a peer-to-peer matching of assets. Without using Liquidity pools, user’s don’t pay transaction fees or incur price slippage. Its transaction ordering is based on optimal execution that is inversely proportional to negative MEV externalities. The transaction ordering is not decentralized and is done by chosen solvers.
Chainlink: Chainlink’s fair sequencing as a service decouples the ability to mine a block from ordering transactions. Instead of a single player deciding the order of transactions, oracle nodes reach consensus on their ordering. This adds an extra layer of consensus and the MEV opportunities may shift to this layer.
Bloxroute: Backrunme is a product provided by bloxroute which essentially provides frontrunning and sandwich protection to users. The transaction is relayed to mining pools that backrun these transactions. A portion of these MEV revenue is given back to the user
BProtocol : It democratizes MEV revenue generated from liquidations. Users interact with lending protocols through BProtocol smart contract. Liquidators or keepers provide backstop liquidity to BProtocol users in return for priority in liquidation transactions. Liquidation MEV revenue is then shared between liquidators and users
Network Based
Flashbots: The most successful organization when it comes to democratizing MEV revenues and reducing its negative externalities is Flashbots. It provides a private auction where traders or users can send bundles of transactions in a private mempool to be executed by miners. This provides them frontrunning protection and also savings in gas fees if the transactions are reverted or failed. Traders or searchers also enjoy a greater share of MEV as they are not engaging in PGAs with generalized bots. Miners get security as well as protection from spam. Flashbots is used by many other dapps and protocols to tackle negative MEV externalities.
MiningDAO: Mining DAO is kind of similar to flashbots with an attempt to decentralize the flashbots auction
Eden Network: Eden network is a transaction priority network for users, block producers and dapps. By staking EDEN tokens, users can get priority and privacy on transactions to get protected from frontrunning and sandwich bots. Block producers get EDEN tokens in addition to Eth block rewards. Dapps can stake EDEN to get priority block space to provide better execution guarantees to their users
Nethermind: Using Nethermind, miners would be able to mine MEV in the same way as Flashbots MEV-Geth client. It supports multiple chains as the client supports a wide range of consensus mechanisms
keeperDAO: keeperDAO employs a hiding game where users route transactions through an off-chain virtual mempool called the hiding book. Keepers or traders who execute arbitrage and liquidation strategies execute these transactions and the MEV revenue is distributed to users and keepers in the form of native ROOK tokens. MEV revenue is democratized between users and keepers(traders). keeperDAO maintains a whitelist of keepers and prevents non-whitelisted keepers from participating thus adding a flavour of centralisation.
Backbone Cabal : It creates a virtualized mempool where a user sends transactions. They batch these transactions for the purposes of arbitrage and other strategies. The MEV revenue is given back to users as cashbacks.
Encryption Based
Sikka : It tackles censorship and frontrunning MEV strategies by threshold encryption. It is a plugin to the core Tendermint BGT engine to create mempool level privacy. Users would be able to submit encrypted transactions which would be decrypted and executed after being committed to a block by 2/3rd of network validators.
VeeDo : VeeDo is StarkWare’s STARK-based Verifiable Delay Function (VDF). VeeDo's time-locks allow information to be sealed for a predetermined period of time (during the sequencing phase), and then made public. This is a time intensive encryption and as MEV strategies are often executed within a block in a very short period of time, this will not allow searchers to execute MEV strategies (even good ones).
LibSubmarine: It is an open source smart contract which protects users from being frontrun using a technique called Submarine Sends which temporarily hides transactions on chain
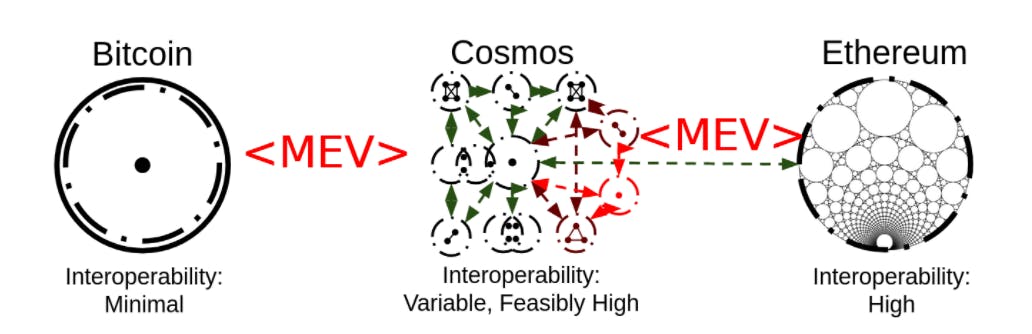
Cross Domain MEV
 (source)
(source)
Domain as described in the paper -A Formalization of Cross-Domain Maximal Extractable Value is ‘a self-contained system with a globally shared state. This state is mutated by various players through actions (often referred to as “transactions”), that execute in a shared execution environment’s semantics’.
Taking the example of different blockchains to be domains, it can be seen that cross-domain interactions increase complexity and programmability. MEV is bound to increase in such an environment and give rise to new vectors of attacks that have never been witnessed before. As transactions interact with chains and protocols having different designs, MEV extractions would become multi-levered. It would also be interesting to see MEV strategies as per varied transaction execution designs. For example, how would MEV depend on the way atomicity is defined on cross-domain transactions. As the points of interaction and value transfer increases, which entities would have more powers of MEV extraction? How dangerous could cross-domain off-chain collusion become? These are questions that would need to be addressed by domain developers in order to come up with a design that allows their dapp builders to tackle predatory MEV behaviours. One of the major questions posed in the paper above is emergence of super traders who can replicate their MEV extraction abilities in multiple domains and have disproportionate influence
Future of MEV
More participation from miners would reveal externalities not observed before
Off-chain collusion, auction of transaction ordering and private mempools would become more prevalent
Better encryption, network and protocol level rules/changes would allow to mitigate risks in a decentralized and effective way
Cross Domain MEVs would become prevalent and reveal new vectors of attacks
